Safety and Security
-
Today’s Connected World
According the United Nations Human Rights Council, access to the Internet is now considered to be a worldwide basic human right. President Obama stated “today, high speed broadband is not a luxury, it’s a necessity.” Our children are growing up in a connected world, and preparing them for that world is an absolutely essential part of education.
The Internet is the largest distribution network for advertising and purchasing of products and services that are both physically and/or digitally delivered. The Internet contains roughly 50 Petabytes (50,000 Terabytes) of RAW UNFILTERED information.
Because of this Internet safety is a critical part of teaching students to use technology.
What does Washington County School District do?
Washington County School District uses a layered approach to filtering that combines prevention with education and remediation. With prevention we use technology based filters and supervision to prevent students from accessing inappropriate content online. With education and remediation we teach students to use the Internet appropriately and responsibly. Internet safety and ethical use is an integrated part in classes taught throughout Washington County School District’s schools.
What resources does to district provide concerning education students on safe internet use and digital citizenship?
These principles are instilled in our children starting at an early age in our elementary labs, where lab aides teach internet safety, privacy and security to all elementary students each year. Students continue through their internet safety education all the way into the graduation required Computer Technology course taught in our secondary schools. We know that teaching kids to use the internet appropriately and responsibly is a critical skill that they will need for the rest of their life.
Many resources to help teach these concepts can be found at http://www.netsafeutah.org/
We also provide extensive educational materials to teachers to be used throughout K-12 that educate students on digital citizenship. We encourage teachers to integrate these digital citizenship lessons into their regular routine as they use technology in the classroom.
In addition many of our schools also take advantage of White Ribbon Week and other digital citizenship programs.
Washington County School District acknowledges that technology based filters are not always effective at eliminating harmful content and due to this, Washington County School District uses a combination of technological means and supervisory means to protect students from harmful online content. To that end, Washington County School District has adopted the 70/30 Rule of Internet Content Filtering.
70/30 rule of internet content filtering
Washington County School District has adopted the 70/30 Rule of Internet Content Filtering. A concept originally developed by Jeremy Cox and presented at the 2015 SAINTCON (https://saintcon.org) Conference (https://youtu.be/32wsQ5VXwWo) by the UtahSAINT Organization (https://utahsaint.org).
The 70/30 Rule of Internet Content Filtering states that students are simply not safe online when only technology measures are used to prevent access to harmful content. This is due to the technical limitations of filtering. As the demand for more security and privacy on the Internet increases, the natural effect of the resulting technological changes directly impairs our ability to filter. The rule of thumb is that 70% of internet content filtering is supervision based, and 30% is technology based. By adhering to the 70/30 rule of internet content filtering the likelihood that a student will be exposed to harmful content is severely reduced.
The concept is simplified and explained in this video:
In order to provide a safe learning environment, WCSD provides supervision for Students when using district devices in the classroom, but must rely on parents to provide supervision for students when outside the classroom.
What filters are being used and how do they work?
Washington County School District currently uses iBoss Cybersecurity’s Secure Web Gateway product to prevent access to unauthorized and harmful content on the web. The iBoss solution was selected from a state wide RFP administered by UETN (Formally UEN). The solution’s subscription is paid state wide by funds administered by UETN. District’s are responsible only for the costs of the appliances.
WCSD currently uses multiple iBoss appliances that filter the outbound traffic leaving the school district’s network. The appliances filter over 7Gbit/sec of internet bound traffic on the average school day. Due to WCSD’s continued commitment of the use of technology in the classroom, the requirements on our network for increased bandwidth grows every year.
WCSD takes the security and protection of our students very seriously, and blocks thousands of websites that host pornographic and other harmful material. The iBoss filtering solution sits on the network, in-line with the District’s outbound internet connection. It actively scans all traffic as it passes across the network, and constantly looks for traffic that is undesirable. When that traffic is detected, it immediately blocks that traffic from passing across the network.
The filter has the capability to block traffic based on the following criteria:
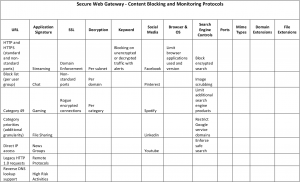
UETN Network Engineering Study, Sanity Solutions,
http://www.uen.org/digital-learning/downloads/UETN_Engineering_Study_Final_Report.pdfIn addition, WCSD utilizes 25 dedicated iBoss Cloud appliances to provide filtering for Chromebooks. This is done by tunneling all internet traffic for each Chromebook through one of the cloud appliances. When the traffic passes through each appliance it is filtered using the same criteria mentioned above. This allows WCSD Chromebooks to be filtered offsite, and support virtual and at home learning with approved programs.
Best practices and technological limitations on filtering.
Unfortunately the mass migration for total encryption on the internet is impairing our ability to filter all harmful content on the network.
“In today’s internet environment, Secure Sockets Layer (SSL) and Transport Layer Security (TLS) encryption, SSL’s replacement, are preventing SWG solutions from identifying traffic content beyond the domain and IP address of its origination. SSL decryption technologies can mitigate some of these issues and allow the SWG solutions to continue performing keyword and individual page filtering. Enabling this feature breaks many applications and services that utilize SSL pinning, it often also requires additional hardware to handle the increased load. As more applications adopt SSL pinning, this option becomes less and less viable. Because of this, few customers are implementing this technology.”
WCSD uses a great deal of services for teaching in the classroom that utilize TLS encryption and SSL pinning. Because of this, we have come to two major realizations:
- It has become unfeasible to decrypt traffic on the network. (and because of this)
- The filter alone is inadequate
To help compensate for this loss, WCSD has adopted the 70 / 30 Rule of Internet Filtering. You can read more about this concept in the section above.
Are there different settings used for different grades and school levels?
Since every teacher and school uses available resources on the internet differently, we have deployed tools within the schools to give the schools greater control of available resources as they deem fit for the students within their school.
How does the district filter internet search engines and other online media?
Because most internet search engines and other online media utilize encryption, WCSD’s filters are unable to view and filter searches on those sites. Because of this, WCSD takes advantage of any services that offered by the individual sites. For example, WCSD uses Google’s Enforced Safe Search, Youtube for Schools, and Microsoft’s Bing in the Classroom. These services, albeit fully encrypted give WCSD some ability to control the content that is delivered through them. Google’s Enforced Safe Search and Microsoft’s Bing in the Classroom give WCSD the ability to toggle a Safe Search flag. In that particular case, WCSD is unable to determine what content is appropriate, and has to rely fully on Google and Microsoft to make those determinations. Youtube for Schools allows us some additional controls, in which we can add to the acceptable list, but the default list is not modifiable by WCSD. Because these services use TLS Encryption and the Google Chromebooks and other Chrome browsers are Pinned to Google’s master certificate, we are unable to provide any more extensive filtering than what is provided through these methods.
WCSD is unable to provide any safe access whatsoever on other encrypted search engines. For this reason, WCSD blocks Yahoo.com, Ask.com, Aol.com, DuckDuckGo.com and other search engines that utilize encryption but do not offer controls to provide some level of safety for our students.
Are there management systems available?
The District utilizes ASE (Active Student Engagement), Google Chromebook Management, and Jamf to manage devices and control their access to the Internet. ASE provides granular local control of internet access on devices and allows teachers and local administration to monitor use and review incidents of students attempting to access inappropriate content.
What is the protocol for students when inappropriate content is accessed?
Each school has been encouraged to develop a Response to Intervention Plan, that identifies the process by which they handle incidents where students use technology inappropriately. The plan creates standards for handing these issues and helps the school provide remediation for the student in a fair and consistent way. Plans are intended to educate students, give them a chance to change and to escalate as incidents become more sever or repetitive.
-
Password Creation Guidelines
Passwords are challenging these days. It is critically important to make a password secure, but sometimes that also makes it hard to remember. We used to believe that to make a password more secure you would add more characters or change some letters to numbers and using a combination of uppercase and lowercase letters. Interesting enough, doing those things doesn’t make it much more difficult for a computer to guess your password. What we knew yesterday about passwords, turns out, isn’t accurate at all. In the end, what makes more of a difference than anything is length.
We use a specific term to measure the strength of a password: entropy. For you math majors, the entropy is calculated by with the following function:

Where E is password entropy, R is the total number of available characters, and L is length.
If your not a math major, the issue is summed up fairly well in this comic from XKCD
(Disclaimer: the password entropy function used in this comic is slightly different, but the concept is still the same)
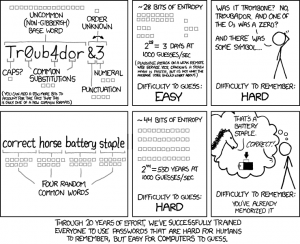
The best password you can make is 20-30 characters long made up of totally random characters. Unfortunately, those are not always very easy to remember, because of that a better solution for most people is a password that is made up of several random words. Long passwords are usually hard to remember, but because your brain only has to remember words instead of letters, numbers, symbols, and other punctuation, these are actually easier to remember, but (because of the length) harder for a computer to guess.
If EFF produced a video that explains this concept and gives you a great idea on how to choose these random words.
Video: How to Make a Super-Secure Password
What are the minimal requirements for WCSD passwords?
Passwords should have at least 70 bits of entropy to meet password requirements. Using this function:

Where E is password entropy, R is the total number of available characters, and L is length.
This equates to:
Passwords consisting of all lower case letters At least 17 characters long Passwords consisting of lower case and upper case letters At least 13 characters long Passwords consisting of lower case letters and at least one number At least 14 characters long Passwords consisting of lower case, upper case letters and at least one number At least 12 characters long Passwords consisting of lower case, upper case letters, at least one number, and at least one symbol At least 11 characters long 
Password Storage Guidelines
-
Why full disk encryption? If your laptop is ever stolen with sensitive data on it, the person who stole it could retrieve every bit of data stored on that laptop, regardless of if it is password protected. It is crucial that any device that contains sensitive data and is transported off district property utilize full disk encryption. With full disk encryption, the data on the device would be worthless to any person who stole it without the users password.
Windows
For Windows first we need to verify that you are running Windows Pro. To verify this we need to run a tool called “System Information”. To do that, you will click on the Start Menu, and then start typing “System Information” without the quotes.
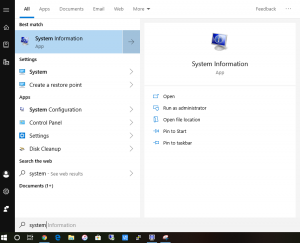
Once you launch System Information, check on the Windows Version located next to OS Name.

Specifically you are looking for the “Pro”. Most computers ordered through a approved District quote should have this.
If you have a “Pro” version of Windows 10 or Windows 8, then you should be able to set up Full Disk Encryption through BitLocker. No, this is not Ransomware, it is a built in Windows utility that provides full disk encryption, that only you can decrypt.
If you don’t have a “Pro” version of Windows, please reach out to the technology department for a quote. Upgrading is inexpensive and easy.
Next, you will want to again click on the start menu and type “Bitlocker”
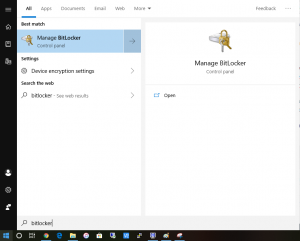
You want to then launch the “Manage BitLocker”.
You should then see the drives you have in your system. You will want to “Turn On BitLocker” on any drive where you store sensitive data. For most of you, this will only be on the C: Drive, or the Operating System Drive.
After you have clicked on “Turn On BitLocker” and authenticated yourself, Windows may ask you to save your private key to your Microsoft account or other location. We recommend you do this so that if for some reason you forget your password, you will not loose access to your files. Afterwards you should see a screen like this:

MAC OS X
In Mac OS X, you will need to start buy clicking on the Apple Menu in the top right hand corner and select “System Preferences…”
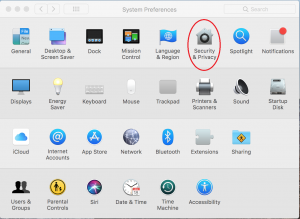
Afterwards, click on the “FileVault” tab at the top, and click “Turn On FileVault”. It will ask you to save a private key, and we recommend that you do that. If not, and you forget your password you will be unable to access your files.
Once everything has been setup correctly, the FileVault panel will look like this:
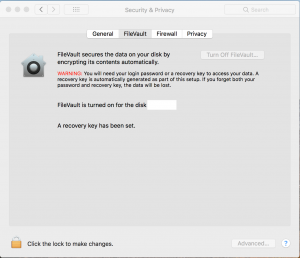
Chromebook
On by default.
iPad
On by default, just make sure to lock your device with a good pass-code (preferably one longer than the standard 4 digits)


